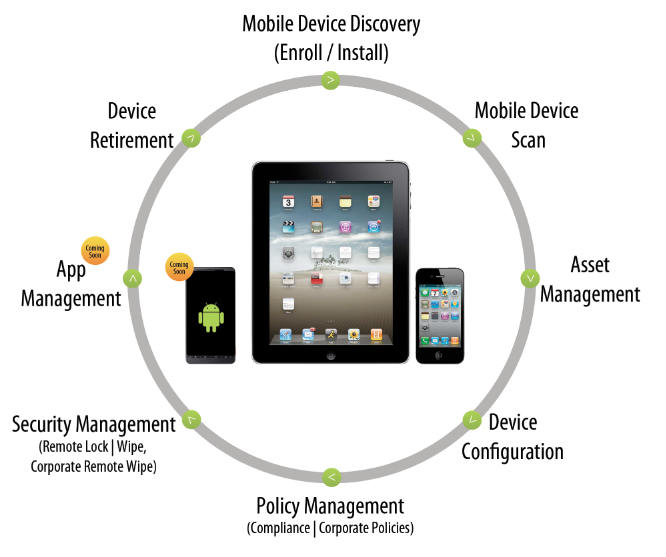
The Need For Mobile Device Management And Security
Like Wi-Fi for operating system updates and also applications downloads Running system updates are commonly significant and also require a great deal of data to be downloaded. It is highly suggested to attach to Wi-Fi during an OS upgrade. This relates to an entire fleet of specialist smart phones in addition to to an individual one.
MTD is developed to spot malware and possibly dangerous mobile applications as well as mobile phishing assaults. It can additionally remediate problems in a selection of ways, consisting of the termination of a link if it recognizes a problem. At an extra technical degree, a mobile danger discovery service can: Monitor a tool's arrangement as well as system parameters and seek suspicious task, such as the modification of system libraries, Inspect the stability of Secure Sockets Layer (SSL) links as well as website certifications and shut down suspicious connections, Diagnose applications that might be "leaking" individual information and find potentially destructive apps via online reputation scanning, code analysis, and malware filtering. With each other, MTD and MDM solutions offer strong safety and security for smart phones and also the network and also applications that they access.
An IT department can develop and manage a work identity on one side of the tool while leaving the other side for personal activities. When a worker leaves a company, IT can wipe the job persona clean without impacting various other material or setups.
Mdm Settings For It Administrators
A mix of mobile threat detection as well as mobile tool management provides maximum security for data and also applications while providing employees the benefits of mobile tools.
Other benefits include:. When a personal mobile gadget is controlled by the MDM server, non-essential applications can be stopped from being made use of during work hours. This will certainly protect against staff members from accessing social networks and other applications while they https://www.livewebdir.com/detail/10419/small-business-it-support-dallas-tx.html are on the clock. When staff members aren't sidetracked by social networks notifications and various other in-app notifications, they'll provide work their full attention and also will certainly be a lot more productive.
MDM solutions can automate this defense across all tools connected to the MDM server. Devices connected to the MDM server can be upgraded, patched, and also managed remotely without disrupting the user's experience. Many thanks to the growing number of innovative cyber safety and security hazards, mobile phone administration is no much longer optional.
What Is Mdm? - Mobile Device Management (Mdm)
Among this group, representing 38% of the grown-up population, we found that: 54% of app users have actually made a decision to not set up a cellular phone app when they uncovered exactly how much personal details they would certainly require to cooperate order to utilize it, 30% of app customers have actually uninstalled an app that was currently on their cell phone due to the fact that they discovered it was gathering personal details that they didn't wish to share. Taken with each other, 57% of all application individuals have either uninstalled an application over concerns about having to share their individual details, or decreased to install an application to begin with for similar factors.
Among this team, we found that: 41% of cell owners back up the images, contacts, and various other data on their phone so they have a duplicate in situation their phone is ever broken or lost, 32% of cell owners have gotten rid of the searching background or search background on their phone, 19% of cell owners have actually shut off the location monitoring attribute on their mobile phone due to the fact that they were concerned that various other individuals or firms could access that information. Also as cell proprietors take actions to preserve control over their personal data in the context of cellphones, the physical gadgets themselves can occasionally fall under the wrong hands.
Although that supporting one's phone is generally carried out as a safeguard in case the phone is lost or taken, cell owners who have in fact experienced a lost or stolen phone disappear likely than average to support the contents of their phone. The youngest cellular phone customers (those ages 18-24) are especially likely to locate themselves in each of these situations.